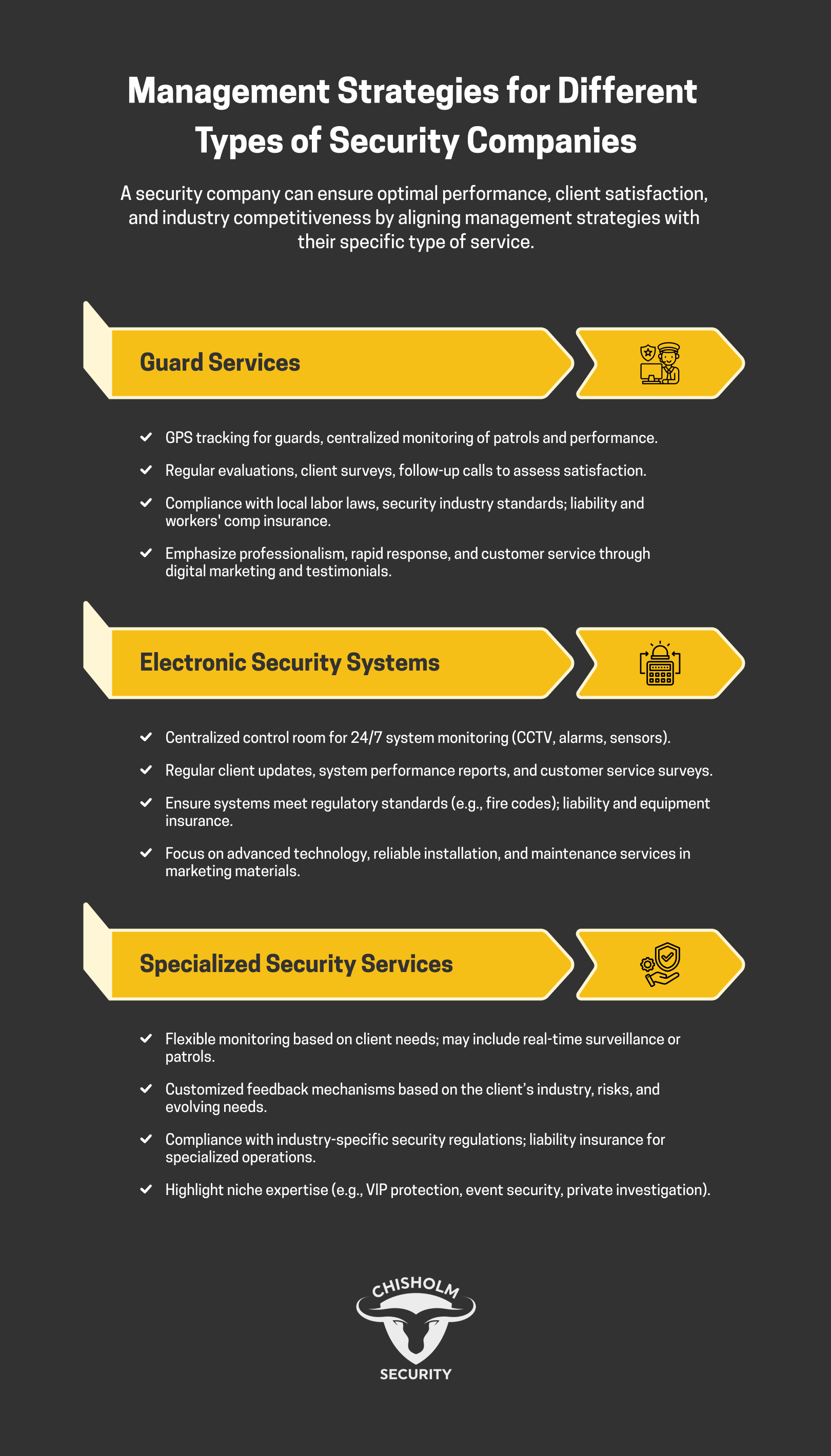
Expert Advice on Managing a Security Company
Managing a security company requires a strategic approach tailored to the specific services offered, whether they be electronic security systems, guard services, or specialized security services. It also demands embracing cutting-edge technologies that redefine how protection is delivered. For instance, video surveillance systems, virtual guards, and integrated monitoring solutions have surged in popularity as businesses seek more efficient, round-the-clock protection.
The global video surveillance software market was worth $56.90 billion in 2022 and is projected to grow at a CAGR of 12.4% from 2023 to 2030. This reflects the increasing demand for advanced technology in the security industry. A forward-thinking security company should focus on integrating new technology as well as implementing proper cybersecurity measures to deal with digital threats.
We also need to invest in comprehensive training programs for our staff. This keeps everyone updated on the latest security practices, enhances the ability to handle situations with professionalism, and establishes clear protocols and proper communication channels with clients and staff. As we manage our resources effectively, including personnel and technology, the company will be better positioned to adapt to market changes and client demands.
Key Takeaways
- Embracing advanced technologies like video surveillance and virtual guards is essential for staying competitive in the modern security industry.
- The growing demand for technology-driven security solutions highlights the importance of integrating these systems into a company’s services.
- Comprehensive staff training and clear communication protocols are vital for maintaining professionalism and adapting to evolving client needs.
Electronic Security Systems
Managing a security company involves effectively incorporating electronic security systems to ensure client safety. Our focus should be on proper installation, maintenance, constant monitoring, rapid response, and keeping up with technological advancements.
Installation and Maintenance
First, the installation of electronic security systems must follow a meticulous plan tailored to each client’s needs. This includes assessing the site, determining weak points, and selecting appropriate equipment such as cameras, sensors, and alarms. Skilled technicians are crucial to installing these systems correctly, avoiding false alarms, and ensuring reliability.
Maintenance is equally important. Regular system checks and software updates prevent potential failures. Timely maintenance can extend the lifespan of the equipment and ensure its operational efficiency. Offering clients a maintenance plan reassures them that their investment is secure and that their system will function optimally.
Monitoring and Response
Monitoring electronic security systems involves constantly overseeing client sites to detect and react to potential breaches. This can be managed through a dedicated control room staffed 24/7. Employing trained professionals to analyze data and respond appropriately is important too.
Response protocols must be established and practiced regularly. Quick responses to alarms, whether they’re false or legitimate, build trust with clients. It’s essential to have a well-documented process for various scenarios, ensuring that our team is ready to act swiftly and appropriately to any incident. Effective communication with local law enforcement and emergency services can enhance our response capabilities.
Technology Updates
The field of electronic security systems is rapidly evolving. Staying current with the latest technology updates keeps us ahead in providing top-notch service. This includes integrating advanced features like AI-driven analytics, remote access, and mobile monitoring capabilities.
AI in video surveillance, for instance, can analyze video footage in real time, detecting anomalies such as suspicious behavior and weapons. It can also analyze historical data to predict potential security risks and proactively implement preventive measures. Chisholm Security also uses remote monitoring for comprehensive real-time surveillance of the premises, which is more effective than traditional guards.
By continuously upgrading our systems, we can offer clients improved security solutions that are both reliable and efficient. Regular training for our staff on new technologies ensures that they are well-versed and capable of handling the latest equipment and software, further cementing our commitment to modern security solutions.
Guard Services
Guard services involve training employees, scheduling shifts, monitoring performance, and managing crises. Each of these areas is essential for maintaining efficient and effective security operations.
It’s important to note that although physical guards can be effective, security companies should also consider incorporating virtual guard services and automated surveillance. On-site guards are limited by human fatigue, coverage areas, and the need for continuous staffing, making them costly and sometimes less efficient. In contrast, virtual remote guard services use technology like video surveillance, AI, and remote monitoring to provide 24/7 oversight without the need for on-site personnel. These virtual services can quickly analyze footage, detect suspicious activity, and respond in real time, offering broader coverage and reducing costs while maintaining a high level of security.
Employee Training
Training is a crucial component of guard services. Our employees must be well-versed in protocols, risk assessment, and various security technologies. We offer a blend of classroom instruction and practical exercises.
We cover emergency procedures such as fire drills and evacuations. Our training programs also emphasize skills like conflict resolution and customer service. Ongoing education ensures that guards stay updated on the latest security methods. Investing in comprehensive training boosts employee confidence and enhances overall security.
Training should extend beyond just physical guards to include operators of video surveillance and virtual security systems. These operators must know how to use the latest technology to effectively monitor and respond to security incidents. Ongoing training also ensures that staff remain updated on industry advancements, helping them leverage emerging technologies for enhanced security management
Shift Scheduling
Effective shift scheduling ensures that our guards are always alert and ready. We use scheduling software to handle complex shift patterns. This helps manage workload and maximize productivity.
We focus on providing adequate rest periods for guards to prevent fatigue. Fair distribution of shifts, including nighttime and weekend duties, ensures job satisfaction. Schedule flexibility can also accommodate guards’ personal needs, reducing burnout and turnover.
Performance Monitoring
Monitoring the performance of our guards involves regular evaluations and check-ins. We use performance metrics to assess reliability, punctuality, and adherence to protocols.
We employ both electronic monitoring systems and on-site supervisory reviews. Feedback mechanisms, including self-assessments and peer reviews, are integral. Performance incentives and recognition programs motivate guards to maintain high standards. Consistent performance monitoring fosters accountability and continuous improvement.
Crisis Management
Crisis management is vital in ensuring our guards respond effectively to emergencies. We develop detailed crisis plans addressing various scenarios like intrusions or natural disasters.
Regular drills and simulations prepare our guards for real-life situations. Clear communication channels are established for rapid information dissemination during crises. Incident reporting and post-crisis analysis help us improve our protocols. Well-prepared crisis management minimizes damage and ensures safety for all.
Chisholm Security video guard system, for example, features a well-established crisis management channel that activates upon detecting an intrusion. When triggered, it relays a live or prerecorded message to caution the intruder while simultaneously assessing the threat level to determine whether it is credible or a false alarm. If a credible threat is identified, authorities are alerted and dispatched immediately, ensuring a swift response to protect all involved.
Specialized Security Services
Effective management of a security company relies on specialized services that cater to a range of client needs.
Customized Protocols
Design customized security protocols tailored to each client’s specific requirements and operational risks. This process involves assessing the client’s assets, threat landscape, and business environment. By understanding these factors, we create detailed response plans that address unique vulnerabilities.
For example, corporate clients might require protection against industrial espionage, while retail businesses may need protocols focused on theft prevention. Specialized protocols ensure that every potential threat is accounted for, providing robust and effective security coverage. Moreover, these protocols are regularly reviewed and updated to adapt to emerging threats and changing circumstances.
Flexibility
In the security industry, the ability to adapt quickly to changing conditions is crucial. We offer flexible service models that can be scaled up or down based on the client’s current needs and risk levels. This might include increasing security personnel during high-risk periods or deploying advanced technology solutions for enhanced surveillance.
By maintaining a flexible approach, we can respond promptly to emergencies or changes in the client’s operational environment. It allows us to deliver efficient and effective security services without compromising quality. Flexibility also encompasses our ability to integrate new tools and methodologies, ensuring our clients benefit from the latest advancements in security technology.
Coordination with Local Authorities
One of the critical aspects of specialized security services is seamless coordination with local law enforcement and emergency services. We maintain strong relationships with these authorities to facilitate effective communication and collaboration during incidents.
For instance, when dealing with large-scale events or emergencies, specialized security service teams work closely with police, fire departments, and medical services to ensure a coordinated response. This cooperation helps in managing incidents more effectively and lessening the overall impact on the client’s operations. Training sessions and joint exercises are also conducted regularly to keep our responses well-aligned with public safety protocols.
Client Confidentiality
Protecting client information is a cornerstone of our specialized security services. We implement stringent confidentiality policies and employ advanced encryption technologies to safeguard sensitive data. This ensures that all client communications and security plans remain secure and private.
Every team member undergoes thorough background checks and receives regular training on confidentiality practices. This helps us maintain high standards of trust and reliability. Client confidentiality extends beyond information protection to include discreet service delivery, ensuring that our presence does not disrupt the client’s regular operations or attract unnecessary attention.
General Best Practices for Managing a Security Company
Effective management of a security company involves real-time monitoring, engaging clients for feedback, ensuring compliance and adequate insurance, and building a strong brand.
Real-Time Monitoring
Real-time monitoring is crucial for any security company. We must use advanced technology and software to keep track of security events as they happen. This helps in promptly addressing any issues, minimizing risk, and increasing client trust.
We need to invest in high-quality live surveillance systems, GPS tracking for patrols, and centralized monitoring centers. By doing so, we can offer a more responsive and reliable service. Additionally, regular audits of these systems ensure they are functioning correctly.
This proactive approach not only safeguards assets but also instills confidence in our clients regarding our services.
Client Feedback
Collecting and analyzing client feedback is a vital aspect of improving our services. We should implement structured ways to gather this feedback, such as surveys, follow-up calls, and online reviews.
Utilizing this feedback allows us to make data-driven decisions to improve service quality. For example, if clients frequently mention a specific concern, addressing it can significantly enhance overall satisfaction.
Regular interaction with clients helps us stay informed about their evolving security needs. This makes it easier to adapt our services to meet those needs effectively and to maintain long-term relationships.
Compliance and Insurance
Compliance with industry standards, local regulations, and surveillance laws is non-negotiable. We must ensure that all our operations meet legal requirements. This includes employee training, equipment standards, and procedural protocols.
Having adequate insurance coverage is equally important. It protects us from liabilities that may arise from unforeseen events. General liability insurance, workers’ compensation, and professional indemnity insurance are must-haves.
Staying updated with regulatory changes and frequently reviewing our compliance and insurance policies will help us mitigate risks and avoid legal complications.
Marketing and Branding
Building a strong brand involves effective marketing strategies. We must develop a unique selling proposition (USP) that differentiates us from competitors. This could be our rapid response time, advanced technology, or exceptional customer service.
We should leverage digital marketing channels like SEO, social media, and email campaigns to reach potential clients. A professional website showcasing our services, client testimonials, and case studies can also enhance our credibility.
Consistent branding across all platforms, including logos, color schemes, and messaging, helps in establishing a recognizable and trustworthy presence in the market.
Transforming Security Management for a Safer Future
In the world of security management, embracing advanced technologies and providing comprehensive training are essential for staying ahead of the competition. By integrating innovative solutions like video surveillance and virtual guards, security companies can enhance their service offerings and ensure reliable protection for clients. Additionally, a commitment to ongoing staff training equips employees with the skills and knowledge needed to navigate the ever-evolving landscape of security threats, fostering a culture of professionalism and responsiveness.
As you consider how to elevate your security management practices, partnering with an experienced security provider can make all the difference. Reach out to Chisholm Security to learn how you can implement state-of-the-art security solutions with expertise and innovation.

