Proven Strategies to Prevent Theft in Your Business
In today’s business environment, theft continues to be a significant concern for many businesses, accounting for about 65% of retail loss and over 70% in some sectors. To protect our assets and ensure the safety of our workforce, it’s crucial to implement effective theft prevention strategies. With the use of video security systems, internal controls, and technology, we can greatly reduce the risk of theft and enhance overall security.
Video security systems act as a powerful deterrent to criminals. Together with virtual guards, they provide an added layer of protection by offering real-time surveillance. Virtual guards can actively monitor footage from multiple cameras, ensuring nothing goes unnoticed. With round-the-clock monitoring, video security can capture suspicious activity as it happens, allowing businesses to take immediate action and reduce the risk of loss.
Understanding the different types of theft, from physical property to digital data, allows us to build a strong foundation for prevention. Combining physical security with advanced technology and management software further solidifies our defense against theft. Thus, we must develop a comprehensive strategy incorporating these elements to maintain a secure business environment.
Key Takeaways
- Leverage video security systems and virtual guards for real-time surveillance and theft prevention.
- Integrate security systems with internal controls and management software for enhanced protection and quick response.
- Develop a multi-layered strategy to safeguard against different types of theft, from physical property to digital data.
Different Types of Theft
Understanding various forms of theft can help businesses implement effective prevention strategies. The main types include retail theft, internal theft, organized retail crime, and employee theft.
Retail Theft
Retail theft, often referred to as shoplifting, involves the unauthorized removal of merchandise from a store. It is a serious type of theft that can significantly affect the profitability of a business. Shoplifters usually use different tactics, such as concealing items in clothing or bags, switching price tags, or simply walking out with unpaid merchandise.
To minimize retail theft, businesses can use security measures like CCTV cameras, electronic article surveillance (EAS) systems, and attentive staff training. Investing in theft-deterrent technologies and creating a culture of vigilance can reduce shoplifting incidents.
Internal Theft
Internal theft is a significant concern, especially when employees are involved. This type usually includes stealing cash, inventory, or sensitive company information. Staff may exploit their access and authority to commit fraud, misappropriate assets, or embezzle funds.
Implementing stringent internal controls is essential. Conducting regular audits, segregating duties, and employing an anonymous reporting system are effective strategies. Detailed record-keeping and monitoring of employee activities can also help identify and mitigate risks.
Organized Retail Crime
Organized retail crime (ORC) involves professional groups that target businesses for significant financial gain. These criminal networks are often sophisticated, using coordinated theft tactics to steal large quantities of goods. ORC can involve staged accidents, receipt fraud, or large-scale shoplifting operations. Over the recent past, ORC perpetrators have been getting more violent–all the more reason why businesses have to be vigilant.
To combat ORC, businesses should collaborate with law enforcement and other retailers. Sharing information about known suspects and theft patterns can help identify and apprehend criminals. Advanced security technologies, such as live remote video surveillance, and thorough employee training to recognize suspicious activities are also beneficial.
Employee Theft
Employee theft encompasses various forms of dishonesty by staff, such as stealing cash, inventory, or falsifying work hours. This type of theft can erode trust within an organization and result in substantial financial losses.
Prevention strategies include thorough background checks during hiring, regular audits, and a strong internal control system. Businesses should consider a good video monitoring system as well. Chisholm Security tailors surveillance solutions to fit specific business needs and infrastructure, from retail stores and warehouses to offices. This can be an effective way to deal with employee theft.
Additionally, encouraging a culture of honesty and integrity, providing ethics training, and implementing clear policies about theft and fraud can deter employees from engaging in such activities. An employee assistance program can address underlying issues that lead to theft too.
Building a Foundation for Theft Prevention
Preventing theft in a business requires a multifaceted approach, combining effective policies, thorough employee training, and robust checks and balances. This comprehensive foundation minimizes risks and safeguards assets effectively.
Creating Robust Theft Prevention Policies
First, we need to create and implement clear and robust theft prevention policies. These policies should outline acceptable behavior, set expectations, and define consequences for violations. It is crucial to ensure these policies are well-documented and accessible to all employees.
In addition to standard policies, specific procedures should address high-risk areas such as cash handling, inventory management, and access controls. Regular reviews and updates to these policies will help keep them relevant and effective against emerging threats.
Engaging employees in the development and review process of these policies drives compliance and accountability. By involving staff, we foster a culture of honesty and transparency.
Employee Training to Mitigate Risks
Employee training is essential in reducing the risk of theft. Comprehensive training programs must cover the specifics of our theft prevention policies and emphasize the importance of adherence. Training should also educate employees on identifying and reporting suspicious behavior.
Regular refresher courses help maintain awareness and ensure continued compliance with policies. We should use a mix of training methods, such as seminars, workshops, and e-learning modules, to cater to different learning styles.
Role-playing scenarios can effectively teach employees how to handle potential theft situations. By educating our team thoroughly, we make them our first line of defense against theft.
Establishing Checks and Balances
Implementing checks and balances is crucial to detect anomalies and deter potential theft. Segregation of duties ensures no single employee controls all aspects of a critical transaction. For example, the person handling cash should not be the same person reconciling accounts.
Regular audits and inventory checks are necessary to identify discrepancies early. These audits should be both scheduled and random to maintain a level of unpredictability. Utilizing technology, such as surveillance cameras and point-of-sale systems, aids in monitoring activities and providing accountability. By combining these controls with our policies and training, we create a strong defense framework against theft.
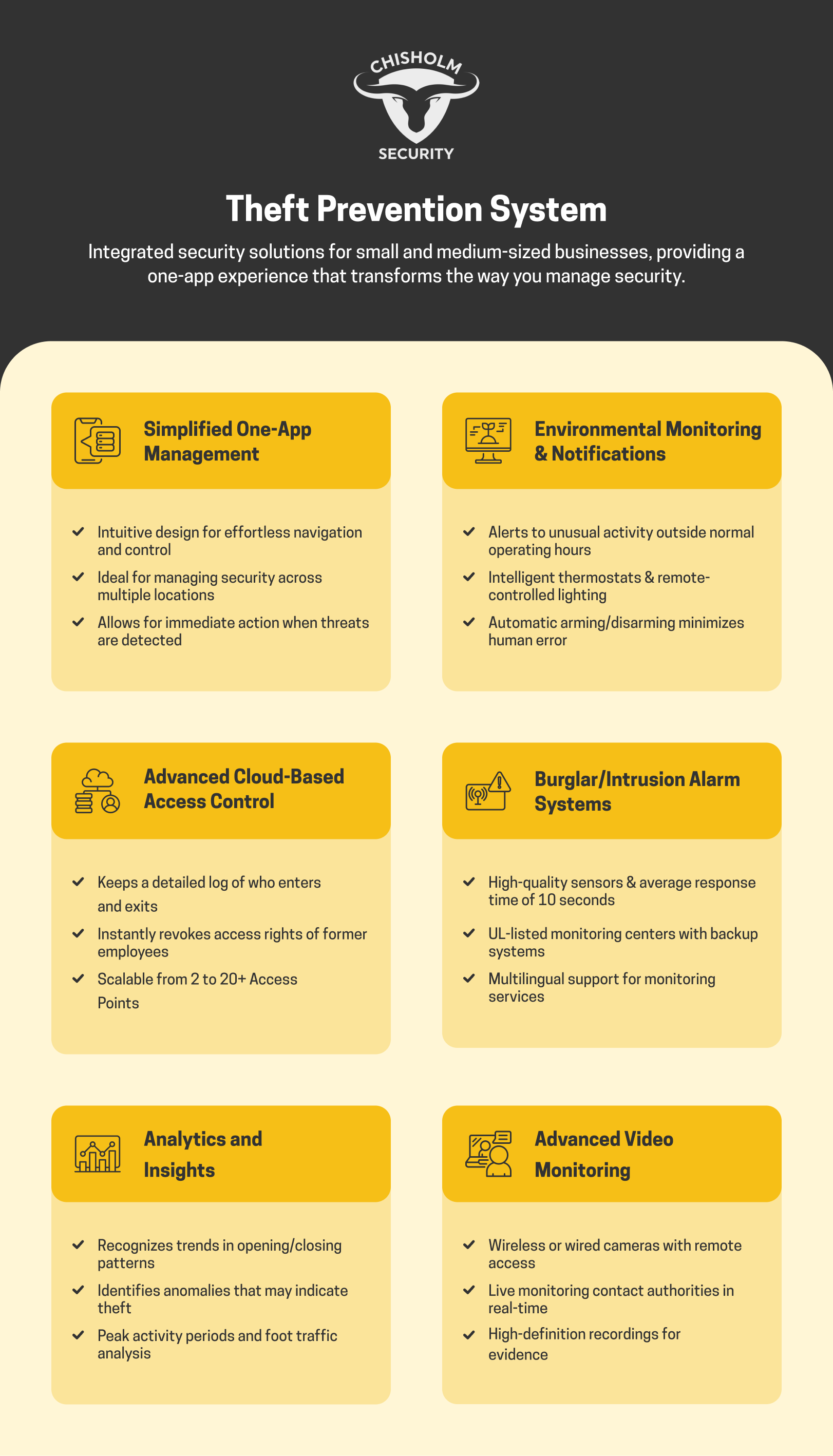
Implementing Video Security Systems
Installing a good video security system is critical for business protection because it acts as a deterrent to potential thieves, provides real-time monitoring capabilities, and ensures strong evidence collection for incidents.
Deterrence
Using video surveillance plays a significant role in deterring theft. When potential criminals notice CCTV cameras prominently placed around a facility, they are less likely to commit crimes. The use of CCTV has proven to be effective in preventing crime. We can further enhance this deterrent effect by placing signs indicating that the premises are under video surveillance. This creates a psychological barrier, making individuals think twice before engaging in illegal activities.
Chisholm Security also incorporates security technologies such as alarm systems and remote guards. Perpetrators are alerted and warned before they commit the crime, reducing the likelihood of theft.
Monitoring
Video security systems allow us to monitor activities in real time. By employing network security measures, we can access live feeds from multiple locations, ensuring comprehensive surveillance coverage. CCTV cameras can be strategically placed to cover high-risk areas, such as entrances, exits, and cash registers.
Real-time video surveillance enables us to spot suspicious activities immediately, enabling prompt response actions. Additionally, integrating these systems with motion-detection technology can trigger alarms and alerts, ensuring our monitoring is always proactive.
Evidence Collection
Collecting evidence is crucial for resolving incidents of theft effectively. Video surveillance provides high-quality recordings that can be used to identify suspects and clarify the sequence of events. We can use CCTV cameras with advanced features like high-definition resolution and night vision to ensure clear footage regardless of lighting conditions. A well-designed network security system helps store video data securely, preventing tampering or loss.
This evidence is invaluable for law enforcement and insurance claims, serving as concrete proof in investigations and legal proceedings. Thus, video security systems significantly bolster our ability to manage and mitigate theft-related issues.
Tactical Internal Controls and Regular Audits
Effective management of internal controls and conducting regular audits are crucial for safeguarding business assets and ensuring the accuracy of financial records. We’ll delve into practical approaches for combating internal theft and the critical role of systematic financial audits.
Implementing Internal Theft Controls
Businesses must establish proper internal controls to deter internal theft such as separation of employee duties as mentioned earlier.
Regular reconciliation is essential. We should frequently compare physical assets with recorded amounts to spot discrepancies promptly. Additionally, using secure, tamper-evident packaging for valuable items can prevent unauthorized access.
Implementing a whistleblower policy can encourage employees to report suspicious activities. We must ensure that such reports are handled confidentially to protect the whistleblower’s identity. Furthermore, investing in training programs about ethical behavior and the consequences of theft can create a culture of honesty and accountability.
For more detailed guidance, the Internal Controls Toolkit offers comprehensive protocols.
The Importance of Regular Audits on Financial Records
Routine audits are vital in maintaining the integrity of financial records. Regular audits help us detect and prevent fraud by thoroughly examining accounting entries and financial statements. We should schedule audits at unpredictable intervals to keep employees vigilant.
Audits should cover all financial transactions. Cross-checking records against external documents such as bank statements ensures accuracy. Hiring external auditors can provide an unbiased perspective on our financial practices and highlight areas for improvement.
Incorporating technology, like audit management software, can streamline the auditing process, making it more efficient. Software tools can quickly identify anomalies and generate real-time reports.
Improving Physical Security Measures
Implementing robust physical security measures is crucial for preventing theft in businesses. Major strategies include controlling access, optimizing store layout, and securing cash handling systems.
Access Control and Key Management
Effective access control is a foundational aspect of business security. We must implement a key management system to maintain control over who accesses restricted areas. Electronic access systems offer enhanced tracking, providing a log of every entry and exit.
- Biometric systems: Utilizing fingerprints or facial recognition to eliminate the risk of lost or stolen keys.
- Access cards: Better than traditional keys as they can be deactivated instantly if lost.
- Audit trails: Monitoring who accessed what area and when helps in identifying security breaches quickly.
Store Layout Optimization
The design of our store layout can significantly impact theft prevention. Strategic placement of merchandise, surveillance systems, and customer service desks helps in deterring potential thieves.
- High-value items: Position these in easily monitored areas or use locked displays.
- Surveillance cameras: Place cameras in both obvious and hidden spots to cover all potential blind spots.
- Mirrors: Use convex mirrors to monitor areas that are not easily visible.
In addition, organizing aisles to avoid creating isolated corners or blind spots can further reduce the likelihood of theft.
Secure Cash Registers
Securing cash registers is another vital theft prevention measure. We must utilize systems that limit unauthorized access and track all transactions meticulously.
- Locked drawers: Ensure that cash drawers are locked when not in use.
- Drop safes: Use drop safes to limit the amount of cash accessible at any given time.
- Real-time monitoring: Implement software, like Chisholm’s video monitoring, that monitors cash register activity in real time to flag suspicious transactions.
Utilizing Technology and Management Software
Incorporating modern technology and specialized management software is critical to reducing theft in business settings. We’ll discuss specific systems that are highly effective.
Inventory Management Systems
Inventory Management Systems (IMS) provide real-time tracking of all goods within a business. By using barcodes or RFID tags, we can monitor the movement of each item from the warehouse to the point of sale. This level of transparency makes it easier to identify discrepancies promptly.
Automated IMS helps mitigate human error and streamline operations. With features like automated reordering and stock level alerts, theft becomes harder to conceal. Additionally, detailed logs and reports offer insights into inventory trends, highlighting unusual patterns that may indicate theft.
Point of Sale (POS) Systems
Point of Sale (POS) systems track transactions and integrate with IMS to maintain up-to-date records. By linking sales to specific employees, POS systems can help identify suspicious behavior. Key features include user access controls and transaction logs.
We can minimize internal theft by assigning unique login credentials and restricting employee access based on roles. POS systems also support various payment methods, ensuring data integrity and reducing manual errors. Reports generated by POS systems are invaluable for auditing purposes, making discrepancies easier to spot.
Loss Prevention Software
Loss prevention software focuses on identifying and minimizing theft, both internal and external. It employs analytics and predictive modeling to detect suspicious activities and trends. By integrating video surveillance with transaction data, we can verify incidents of theft more effectively.
Features like exception-based reporting allow us to flag irregular transactions and inventory movements. Machine learning algorithms can predict high-risk periods and areas within the business. With these capabilities, the software provides actionable insights, enabling proactive measures to prevent theft.
Developing a Comprehensive Prevention Strategy
A strong approach to theft prevention requires regular security updates, thorough risk assessments, and active employee participation. These strategies help ensure robust protective measures and a culture of vigilance within the business.
Regularly Review and Update Security Measures
Constantly reviewing and updating our security protocols is pivotal. We need to stay ahead of evolving threats by incorporating the latest technologies and methodologies. This includes upgrading surveillance systems, implementing more effective access controls, and ensuring our alarm systems are functioning optimally.
We should also train staff on new security measures promptly. Regular audits can highlight inefficiencies and vulnerabilities that need addressing. By maintaining an up-to-date security framework, we can greatly reduce the risk of theft.
Conduct Risk Assessments
Conducting risk assessments helps identify potential security weaknesses. We need to evaluate all aspects of our business, from physical infrastructure to digital asset protection. Assessing risks means examining entry points, employee workflows, and even our cybersecurity posture.
Periodic risk assessments allow us to implement targeted measures to mitigate identified threats. This proactive approach can involve everything from reinforcing physical barriers to fortifying our network security. Consistent risk evaluations keep our preventative strategies robust and pertinent.
Engage Employees in Prevention Efforts
Our employees play a crucial role in theft prevention. Engaging them in our security efforts enhances overall effectiveness. We should provide thorough training on recognizing suspicious behavior and understanding proper security protocols.
Encouraging a culture of awareness ensures that all team members are vigilant and active participants in safeguarding our assets. Implementing anonymous reporting systems can help employees report concerns without fear of retribution. When everyone is committed to maintaining a secure environment, the likelihood of theft diminishes significantly.
Building a Lasting Defense Against Theft
Preventing theft in your business is not a one-time task; it requires ongoing vigilance and a comprehensive strategy. By combining modern video security systems with internal controls and regular audits, you can establish a strong, effective defense against both internal and external theft. Educating your team and fostering a culture of integrity further strengthens this security framework, ensuring that your business is protected from potential losses.
Chisholm Security is a trusted provider of video security systems. Our customizable solutions offer real-time surveillance and proactive protection, helping you safeguard your assets and maintain peace of mind. Learn more about how Chisholm Security can help secure your business by visiting chisholmsecurity.com.

