Key Considerations When Upgrading Your Security System: Essential Factors for a Modern Setup
Modern security solutions offer a wide array of features that were once unavailable or prohibitively expensive. From smart home integration to facial recognition and remote monitoring, these innovations can transform your security setup.
Before diving into the latest gadgets and gizmos, it’s essential to assess your current security vulnerabilities and future requirements, guide your upgrade process, and help you prioritize investments and avoid unnecessary expenses. Let’s explore the critical aspects of upgrading your security system to create a safer, more secure environment.
Key Takeaways
- Assess current vulnerabilities and future needs before upgrading
- Consider compatibility with existing equipment and smart home integration
- Ensure compliance with local regulations and plan for proper maintenance
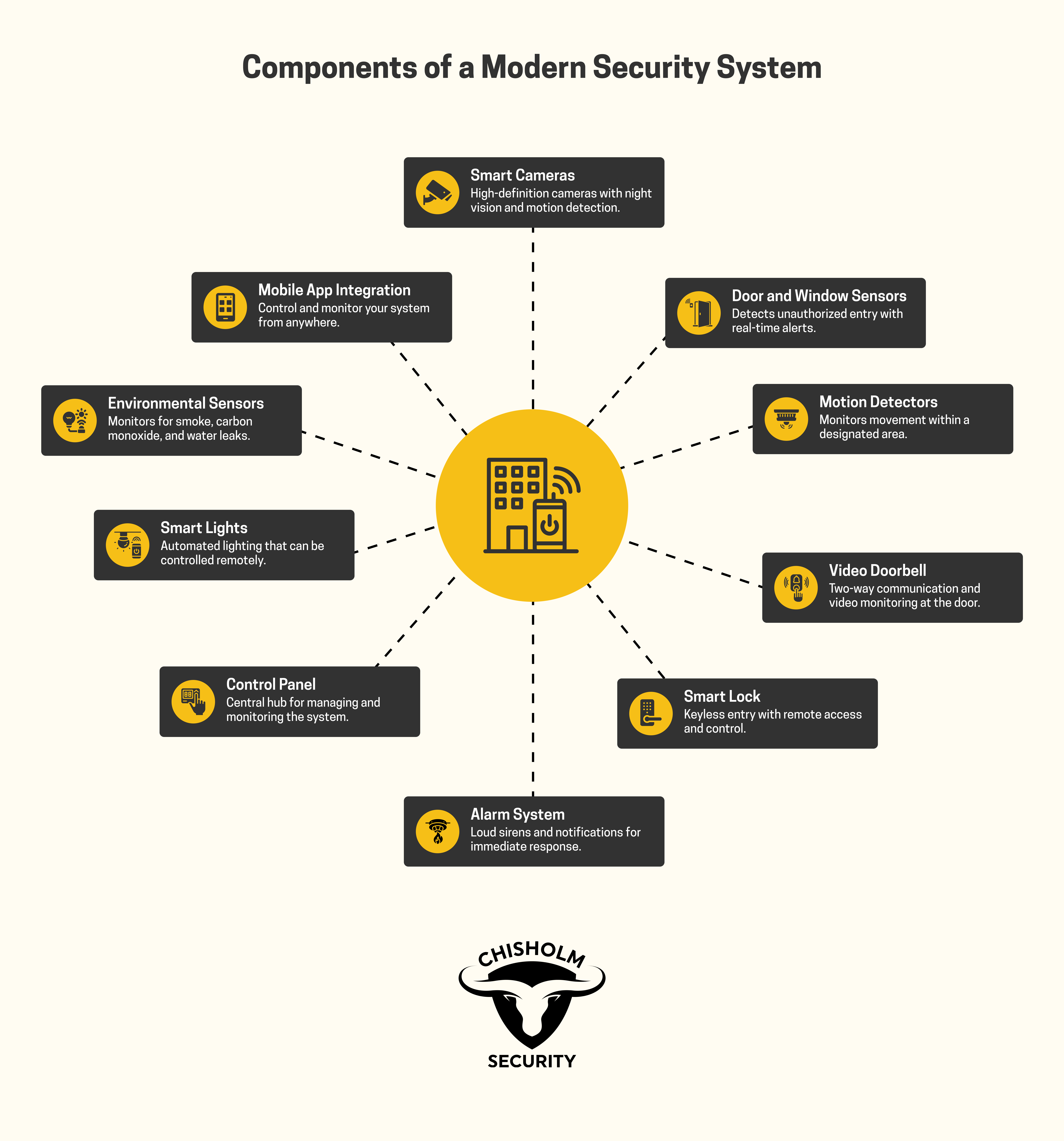
Evaluating Current Security Needs
Upgrading your security system requires a thorough evaluation of your current infrastructure and the identification of any gaps or vulnerabilities, ensuring that your system is not only up-to-date with modern technology but also compliant with industry-specific regulations. Here’s a step-by-step guide and checklist to help commercial properties effectively assess their security needs, along with recommendations for tools and software that can facilitate this process.
Step 1: Comprehensive Audit of Existing Security Infrastructure
Checklist:
- Inventory of Equipment:
- List all security cameras, alarm systems, access control devices, and monitoring services.
- Note the model, age, and current condition of each device.
- Performance Evaluation:
- Test each device to assess its functionality, image quality, and response time.
- Identify any recurring issues, such as false alarms or connectivity problems.
- Compatibility Check:
- Determine if the existing equipment supports modern encryption protocols.
- Check integration capabilities with current business management systems (e.g., ERP, CRM).
- Regulatory Compliance:
- Ensure that all components meet industry-specific regulations such as HIPAA, PCI-DSS, or GDPR.
- Review data storage and handling practices to confirm compliance.
Tools and Software Recommendations:
- Security Risk Management Software: Tools like Resolver or Everbridge can help document and analyze the performance of existing security components.
- Compliance Management Tools: Netwrix Auditor and SolarWinds offer solutions to assess and ensure compliance with industry regulations.
- Asset Management Systems: Utilize software like Ivanti or ManageEngine to track and manage all security assets efficiently.
Step 2: Identifying Security Gaps
Checklist:
- Physical Security Assessment:
- Inspect all entry points, including doors, windows, and loading docks, for vulnerabilities.
- Evaluate the effectiveness of lighting around the property, particularly in parking areas and secluded spots.
- Check the placement of security cameras for blind spots or insufficient coverage.
- Technological Vulnerability Scan:
- Perform a cybersecurity assessment to identify any risks related to your networked security systems.
- Ensure that all software, including firewalls and anti-virus programs, is up-to-date.
- Test the integration of AI-powered analytics and remote access features.
- Operational Review:
- Review current security protocols, including alarm response procedures and incident reporting.
- Evaluate staff training on using security systems and responding to emergencies.
- Assess the scalability of the current system for future expansions or additional business locations.
Tools and Software Recommendations:
- Vulnerability Scanning Tools: Use Nessus or Qualys to conduct thorough scans of your networked security systems to identify potential cyber threats.
- Surveillance Analysis Software: Milestone XProtect or Genetec Security Center can help analyze camera coverage and identify blind spots.
- Physical Security Information Management (PSIM): Platforms like Pro-Watch by Honeywell or CNL Software offer comprehensive solutions to monitor and manage physical security systems.
Step 3: Developing an Action Plan for Upgrades
Checklist:
- Prioritize Upgrades:
- Based on the audit and gap analysis, prioritize the areas that need immediate attention.
- Develop a phased implementation plan, starting with the most critical vulnerabilities.
- Budget Planning:
- Estimate the cost of required upgrades, including hardware, software, installation, and ongoing maintenance.
- Explore financing options or phased implementation to manage costs effectively.
- Integration Strategy:
- Plan for the integration of new systems with existing infrastructure.
- Ensure that upgrades are compatible with future technologies and business expansions.
Tools and Software Recommendations:
- Project Management Tools: Software like Microsoft Project or Asana can help plan and track the implementation of security upgrades.
- Cost Estimation Tools: RSMeans Data Online provides accurate cost estimates for security equipment and installation.
- Integration Platforms: Edge AI platforms like EdgeX Foundry or ThingWorx can facilitate the integration of new security technologies with existing business systems.
Evaluating your current security needs ensures that your commercial property is well-protected against evolving threats. By following this detailed guide, you can systematically assess your existing setup, identify any gaps, and develop a strategic action plan for upgrades. The use of specialized tools and software further enhances the accuracy and efficiency of this process, ensuring that your security system is both robust and compliant.
Understanding New and Emerging Technologies
New technologies are revolutionizing security systems, offering enhanced capabilities and integration. These advancements provide improved protection and convenience for users.
The Impact of AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing the security landscape, offering enhanced capabilities for threat detection and system management. AI-powered systems can analyze patterns and anomalies in real time, reducing the likelihood of false alarms and increasing the accuracy of threat identification.
For instance, AI-enhanced facial recognition systems can be crucial for businesses that need to control access to sensitive areas, such as data centers or executive offices, quickly identifying unauthorized personnel and triggering alerts, allowing security teams to respond promptly. Furthermore, ML algorithms can adapt to changing environments, making your security system more resilient over time.
The predictive analytics capabilities of AI also offer significant benefits. By analyzing historical data, these systems can anticipate potential security breaches and suggest proactive measures, improving overall security and helping maintain compliance with regulations that require advanced security measures, such as the Sarbanes-Oxley Act for financial reporting integrity.
Integration With Smart Home Features
The integration of smart technologies with security systems has become increasingly important, especially for businesses looking to streamline operations and enhance security. Smart home features, such as voice-controlled systems and automated lighting, offer convenience and efficiency. However, for businesses, the focus should be on how these features contribute to overall security and regulatory compliance.
For example, smart locks integrated with your security system can ensure that only authorized personnel access sensitive areas. Automated lighting systems can be programmed to activate in response to detected motion, reducing the risk of break-ins during non-business hours. Additionally, smart thermostats and environmental sensors can provide alerts for potential hazards like fire or gas leaks, enhancing both safety and regulatory compliance.
However, integrating these features requires careful planning to ensure compatibility with existing systems and adherence to security best practices. Systems like those offered by Chisholm Security are designed to integrate seamlessly with a wide range of smart technologies, ensuring that your business enjoys the benefits of modern innovation without compromising security or compliance.
Advances in Cameras and Surveillance
Surveillance technology has made significant strides in recent years, offering businesses powerful tools to enhance security. Modern cameras now offer ultra-high-definition (4K) resolution, providing clear images that can be critical for identifying intruders or investigating incidents.
For multi-site operations, wide-angle and panoramic cameras can provide extensive coverage, reducing the number of devices needed and simplifying management. These cameras, when combined with advanced analytics software, can monitor large areas and flag unusual activities, such as unauthorized access to restricted zones.
Night vision and thermal imaging capabilities have also seen substantial improvements, allowing for effective surveillance in low-light conditions, which is particularly important for businesses operating 24/7 or in areas with minimal natural light. Moreover, cloud storage solutions ensure that surveillance footage is securely backed up off-site, protecting data even in the event of physical damage to the cameras.
The integration of two-way audio with surveillance systems enables real-time communication, which can be crucial for security teams managing multiple sites, allowing security personnel to issue warnings or communicate directly with individuals on the premises, potentially deterring criminal activity.
Benefits of Upgrading Your Security System
Upgrading your security system offers significant advantages in monitoring capabilities and emergency response. Modern systems provide enhanced functionality and peace of mind.
Enhanced Monitoring and Remote Access
One of the most significant benefits of upgrading your security system is the ability to monitor and control your system remotely.
Remote access allows you to view live camera feeds, receive alerts and control system features like door locks and lighting from any location. For instance, a retail chain can monitor security across all its stores from a single control center, ensuring consistency and quick response times.
The ability to arm or disarm the system remotely adds an extra layer of convenience, especially for businesses that operate outside of traditional hours, allowing integration with other business systems, such as inventory management or HR platforms, providing a holistic view of operations and security.
Improved Safety and Emergency Response
Modern security systems offer faster, more accurate emergency responses, which is crucial for businesses that need to protect both physical assets and sensitive data. Advanced sensors can detect not just intrusions but also environmental hazards like fire or carbon monoxide, triggering immediate alerts and automated responses.
For example, in a data center, an integrated security system could automatically shut down servers and activate fire suppression systems in the event of a fire. Such proactive measures not only protect valuable assets but also ensure compliance with safety regulations, such as those outlined by OSHA.
The inclusion of two-way communication with monitoring centers allows for immediate interaction between security teams and first responders, further reducing response times and increasing the chances of mitigating damage or loss.
Integration and Compatibility Considerations
When upgrading your security system, you must ensure seamless integration with existing devices and future-proof your setup. Compatibility with smart home technologies and legacy systems can greatly impact the effectiveness and longevity of your security solution.
Smart Device and Home Automation Compatibility
When upgrading your security system, you must ensure compatibility with existing smart devices and home automation platforms. For businesses, this means choosing systems that can integrate with building management systems, access controls, and even customer management tools.
For instance, a hotel might integrate its security system with its room management system, allowing for automated check-ins and enhanced guest security. Similarly, smart lighting and HVAC systems can be connected to the security system to optimize energy usage while maintaining security protocols.
Chisholm Security offers systems that support a wide range of protocols, ensuring seamless integration with your existing infrastructure. This compatibility not only enhances security but also allows for more efficient management of business operations.
Legacy Systems and Future-proofing
Upgrading a security system doesn’t always mean starting from scratch. Many modern systems are designed to work with existing equipment, allowing businesses to upgrade in phases and spread out costs.
For businesses planning expansions, modular systems work well, allowing for the addition of new devices without overhauling the entire system. Regular software updates also maintain system security and functionality, ensuring compliance with evolving regulations.
Wireless systems offer flexibility in installation and expansion, making them a good option for businesses with dynamic layouts or multiple locations. Systems that operate independently of the internet maintain security during outages.
Planning and Budgeting for Security Upgrades
Effective planning and budgeting are crucial for successful security system upgrades. We’ll explore cost considerations and deployment strategies to help optimize your investment.
Includes Cost Savings and Pricing
Upgrading your security system is an investment that can yield significant cost savings in the long run. By integrating security with other business systems, you can reduce operational inefficiencies and improve overall productivity.
For example, cloud-based security solutions often have lower upfront costs and provide flexibility for businesses with fluctuating needs. Additionally, upgrading to a system that meets or exceeds industry standards can reduce insurance premiums and liability risks, resulting in further savings.
When budgeting for an upgrade, consider not just the cost of new equipment but also installation, maintenance, and potential downtime during the transition. Partnering with a security provider like Chisholm Security can help streamline this process, ensuring that your upgrade is both cost-effective and minimally disruptive to your operations.
Developing a Deployment Plan
A well-structured deployment plan is critical for the successful implementation of security upgrades, particularly in industries with strict regulatory requirements or businesses experiencing rapid expansion. A comprehensive approach ensures not only the technical installation of new systems but also strategic alignment with compliance obligations, scalability demands, and seamless integration with existing business systems.
- Assessment and Gap Analysis
Begin by conducting a thorough assessment of your current security infrastructure. This process involves identifying existing vulnerabilities, understanding compliance requirements specific to your industry, and evaluating how well your current systems meet these needs. For example, a healthcare facility must consider HIPAA regulations, which mandate the secure handling of patient data. At the same time, financial institutions must adhere to GLBA guidelines that require robust data protection measures.
- Prioritizing Upgrades Based on Risk and Compliance
Once vulnerabilities are identified, prioritize security upgrades based on a combination of risk assessment and compliance requirements. For instance, a company managing multiple locations might prioritize systems that enable centralized, remote monitoring, allowing security teams to oversee multiple sites from a single platform. Chisholm Security’s advanced surveillance systems, designed to integrate with existing infrastructure and comply with various regulatory frameworks, can be a strategic solution here, ensuring enhanced security and regulatory alignment.
- Phased Implementation with Pilot Testing
Implementing security upgrades in phases is often the most effective way to minimize disruptions to daily operations. For example, large businesses might begin by upgrading the security systems at their most critical sites first, using these as a pilot before rolling out the solution company-wide. This phased approach not only allows for troubleshooting and optimization but also ensures that each phase meets the specific compliance requirements of different locations or operational areas.
- Cross-Departmental Coordination
Security system upgrades often require coordination across multiple departments, including IT, facilities management, and legal. Ensuring that the new system integrates seamlessly with other business operations can prevent potential conflicts and ensure that all compliance requirements are met. For instance, integrating physical security with an IT department’s cybersecurity infrastructure creates a comprehensive security posture that addresses both physical and digital threats.
- Training and Support
Training is a crucial component of any security system upgrade. Employees need to be familiar with the new system’s features, especially if these include advanced functionalities such as AI-driven threat detection or automated access controls. Regular training sessions and refresher courses ensure that staff remain proficient in using the system, thereby maximizing its effectiveness.
- Project Management and Oversight
Designating a project manager with a deep understanding of both the technical and regulatory aspects of the security upgrade can significantly enhance the likelihood of success. This individual should be responsible for ensuring the project adheres to the timeline and budget, as well as for coordinating regular progress reviews. These reviews provide opportunities to address any issues promptly and to adjust the plan as necessary to ensure that the upgrade meets both operational and compliance goals.
Security System Installation and Setup
The installation and setup of a security system are critical phases that determine the overall effectiveness and longevity of the solution. The decision between professional installation and a DIY approach can significantly impact both the system’s performance and compliance with industry regulations.
Professional Installation vs. DIY
Professional installation offers a level of expertise that is particularly valuable for businesses with complex security needs or those operating in regulated industries. For example, Chisholm Security’s certified technicians can perform a comprehensive site assessment to recommend optimal sensor placements and ensure proper wiring and connections to maintain compliance with regulations like PCI DSS in financial institutions or HIPAA in healthcare settings.
DIY installation may be a viable option for smaller businesses or less complex environments, particularly those with a lower regulatory burden. However, this approach requires a significant time investment and technical know-how. Improper installation can lead to security gaps that may not only expose the business to risk but also result in non-compliance with industry regulations, leading to potential fines or legal action.
Configuring Security Features
The configuration of security features is a critical step in the installation process that can greatly impact system performance and compliance. Proper configuration includes setting up user accounts with appropriate access controls, adjusting motion sensors to avoid false alarms, and integrating the system with existing business management platforms or smart devices.
For businesses with multiple locations, configuring remote monitoring capabilities allows centralized oversight of all sites, enabling security personnel to respond quickly to incidents and ensuring consistent application of security policies across all locations. Chisholm Security’s solutions offer robust configuration options, including customizable alerts and geofencing features tailored to meet the specific needs of multi-site operations.
Maintaining Your Upgraded Security System
Ongoing maintenance is essential to ensure the continued effectiveness and compliance of your security system. Regular checks, updates, and professional support services help prevent system failures and ensure that the system remains aligned with regulatory requirements.
Routine Checks and Firmware Updates
Weekly visual inspections and functionality tests of all security devices identify any physical damage, loose connections, or signs of tampering. Regular firmware updates improve system performance and address potential security vulnerabilities.
Ongoing Support and Maintenance
Establishing an ongoing relationship with a professional security provider, such as Chisholm Security, ensures that you have access to support and maintenance services whenever needed. Regular professional inspections can identify potential issues before they become critical while having spare parts on hand allows for quick replacements, minimizing downtime, and maintaining compliance with industry standards.
For businesses in highly regulated industries, regular audits of the security system are essential. These audits should include a review of security protocols, access logs, and incident reports to ensure that the system continues to meet all relevant regulatory requirements.
Legal and Compliance Issues in Security
Upgrading your security system involves navigating a complex landscape of legal and compliance requirements, particularly in industries with stringent regulations.
Compliance with Industry-Specific Regulations
Different industries have unique regulatory requirements that dictate specific security measures. For example, healthcare organizations must comply with HIPAA, which includes strict requirements for the protection of patient data. At the same time, financial institutions are required to adhere to PCI DSS standards for the secure handling of payment information.
When upgrading security systems, businesses must ensure that all new components and configurations comply with these industry-specific regulations by implementing advanced encryption methods, setting up secure data storage solutions, or configuring access controls to limit data access to authorized personnel only. Chisholm Security’s systems are designed to meet or exceed these compliance requirements, providing businesses with the tools needed to protect sensitive information and avoid regulatory penalties.
Legal Implications of Security Measures
In addition to compliance, businesses must consider the broader legal implications of their security measures, including understanding the legal boundaries of employee monitoring, ensuring that data collection practices comply with privacy laws like GDPR or CCPA, and preparing for potential liabilities in the event of a security breach.
Regular audits and assessments maintain compliance and mitigate legal risks. Include a review of security policies, procedures, and system configurations to ensure that all aspects of the security system align with legal requirements and best practices.
By addressing these legal and compliance issues as part of your security upgrade, you can protect your business from regulatory penalties and legal liabilities while ensuring a high level of security for your assets and data.
The Future of Security: Why It’s Time to Upgrade
Upgrading your security system is a strategic investment in the safety and longevity of your business. From AI-driven analytics to smart home integration, modern security systems offer unparalleled protection and convenience. However, the success of these upgrades hinges on careful planning, professional installation, and ongoing maintenance.
At the heart of this upgrade lies the need for a system that meets today’s standards and is adaptable to future challenges. Whether it’s enhancing your surveillance capabilities, integrating smart technologies, or ensuring compliance with industry regulations, a well-executed security upgrade can provide long-term peace of mind and operational efficiency.
Ready to take your security to the next level? Contact Chisholm Security today to learn how our expert installation services can help you achieve a setup that maximizes effectiveness while minimizing the risk of gaps or blind spots. Secure your future with a system designed to protect what matters most.cessary regulations.

